Gone are the days when cyberattacks required actual skill. The latest HP Wolf Security report: “The Evolution of Cybercrime: Why the Dark Web is Supercharging the Threat Landscape and How to Fight Back” shows the ease with which cheap malware kits are being shared on the dark web.
“Digital transformation has supercharged both sides of the attack-defence divide – shown, for instance, by the increasing popularity of ‘as a service’. This has democratised malicious activity to the point where complex attacks requiring high levels of knowledge and resources – once the preserve of advanced persistent threat (APT) groups – are now far more accessible to a wider group of threat actors,” says Alex Holland, Senior Malware Analyst at HP Wolf Security’s Threat Research team – and author of this report.
Barrier to Entry
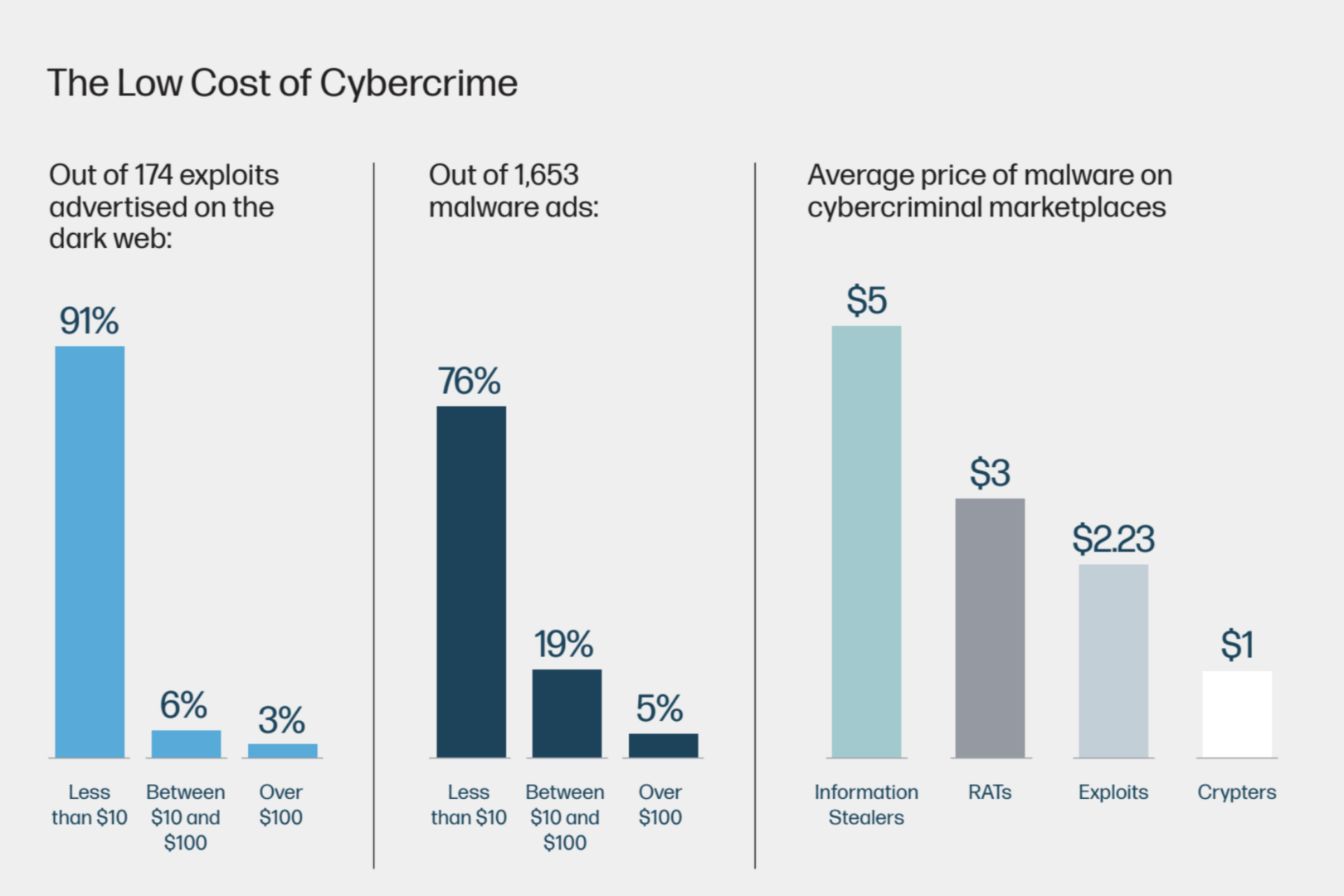
On top of malware being available as kits with tutorials and mentoring groups, their price point has seen a race to the bottom. 91% of exploits and 76% of malware kits were advertised as priced below $10. Dark web marketplaces function like well-organised ecom brands with escrow guarantees and reviews.
 “Back in the day, you had to figure stuff out yourself and show off what you could do technically to be noticed. Today, only a small minority of cybercriminals code, most are just in it for the money – and the barrier to entry is so low that almost anyone can be a threat actor. That’s bad news for businesses.”
“Back in the day, you had to figure stuff out yourself and show off what you could do technically to be noticed. Today, only a small minority of cybercriminals code, most are just in it for the money – and the barrier to entry is so low that almost anyone can be a threat actor. That’s bad news for businesses.”
Michael Calce, HP Security Advisory Board Chairman and former hacker “MafiaBoy.”
Education is paramount
“The channel can help customers escape this game of Russian roulette by bringing them technologies that isolate these common threat vectors at the hardware level, neutralising such attacks regardless of whether they can be detected – thus resulting in a greatly reduced attack surface and far more resilient security posture,”
Ian Pratt, Global Head of Security for personal systems at HP.
He continued by saying that staff devices continued to be the key entry point for attackers into an organisation and that partners could inform clients and assist in shielding people from email phishing schemes and web-based attacks.
What can be done?
In addition to the dire cautions on the spread of malware, HP also offered some user guidance:
Learn the fundamentals: Using multi-factor authentication and patch management, you can lower your risk of being attacked. Additionally, measures could be implemented to lessen the attack surface for file downloads, web browsing, and email.
Be ready for the worst: Establish procedures to examine supplier security and train workforces on social engineering to reduce the danger posed by partners and staff.
Share data: Talk to your colleagues to exchange information and share knowledge of threats in real-time.